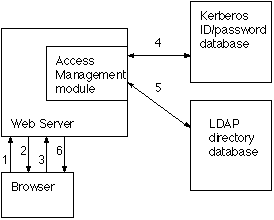
When a user from outside the network requests access to an object, there are several steps that occur. Below is an example of a simple web access management solution.
- User requests access to an object
- The web server requests credentials
- The user supplies their credentials
- The WAM module verifies the user's credentials with a validation service (Kerberos in this case)
- The WAM loads the attributes of the identity
- The web server provides the requested resource
The WAM software is typically a plug-in for a web server, and functions as the gateway from the web into the corporate web based resources. A useful feature is that WAMs usually allow for single sign-on. That way, once a user is authenticated, they are able to use several different resources without having to log in multiple times. The WAM is able to do this by maintaining a constant session with the user so that it can check the user's permissions whenever requesting a new object. This is achieved by issuing a cookie which the user's browser can easily supply when requested. Once the session is over, the cookie is erased and the browser no longer has access until re-authenticated.
No comments:
Post a Comment